What is router?
A router is a device that helps to transfer the data and information from a network to the other network. It also does many changes to the data so that they can easily transfer.
What does a router really do?
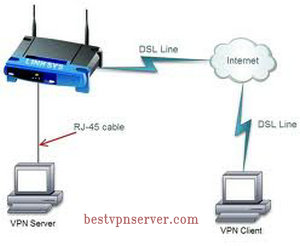
It normally takes some information in it and then transfer them through the routes which will be easier for them to pass through.
This is a device that resembles with other devices like hub, switch but the function of router is more than the others. Like the other devices can only transfer the data or make it passing through the other network. But the router not only transfer the data it does so many changes like analyzing them and find out the best way to transfer them in the quickest time.
The router does the following jobs
· It helps to restrict the broadcasts. When broadcast communication works then a lot of devices work together to transmit the data. But it creates collisions. So the router helps to separate the hosts and help them to transfer in another way.
· It acts as a default gate way. When you are trying to communicate with the another computer the router receives the data and then it search for the computer or another network and then the router transfers the data.
· It helps to move data from a network to the other network even if they are from two different organizations.
· It just do some study on the data and then send them to the loop free path to pass them freely and quickly.
VPN for router:
As we know that VPN which means Virtual Private Network helps to unlock , unblock the blocked sites and also increase the security of the data. So the people who want to make their activity private they all use the VPN service. Specially in the router through which people share the important files and information to one computer to the other. They like to do it privately and securely. So for them VPN is a great solution.
There are different types of VPN for router. Mainly two types of VPN are mainly used. They are
*Pro VPN PPTP setting
*Open VPN for DD-WRT
Setting for Pro VPN PPTP setting:
To do this setting the router must have DD-WRT firmaware installed.
Then you need to go to the set up panel. There you will have to select WAN set up and then select the connection type PPTP and then filling the box of the username of the VPN account and password of the PPTP all will be set for using the router through VPN.
Setting for Open VPN for DD-WRT:
The router need to have DD-WRT firmaware installed..
It must be Open VPN capable. Then firewall must be turned off and a modem is plucked by WAN port. The router should be reset like 30/30/30. The ISP must be asked to open some ports of the modem.
Finally the four steps setting up the date time, downloading the start up script, cop paste the contests and rebooting you can start using the router through VPN.
Find a VPN compatible router
You may prefer to setup a VPN connection on your actual router.After Configure VPN connection on your router and all devices connected to your network,All the data will be routed through VPN server .
By doing that,you have to find a VPN compatible router,So you can
1.play online games on Games consoles like Xbox, PS3, Wii.
2.Watch popular video streaming on Apple TV or Netflix devices
3.Other mobile devices for Home entertainment
Here are some good VPN compatible router you can choose,
Cisco Linksys WRT54GL,Cisco Linksys E4200v2 Maximum Performance Dual-Band N900 Router,Asus RT-N16,Asus RT-N66U Dual-Band N-900 Wireless Router and D-Link DIR-320 A1/A2/DIR-600 B1/B2.You also can easily find the VPN router on amazon.
Cisco Linksys WRT54GL,Cisco Linksys E4200v2 Maximum Performance Dual-Band N900 Router,Asus RT-N16,Asus RT-N66U Dual-Band N-900 Wireless Router and D-Link DIR-320 A1/A2/DIR-600 B1/B2.You also can easily find the VPN router on amazon.
From,
http://www.bestvpnserver.com/vpn-routers-to-vpn-server-on-home-devices/